Welcome to the December release of Atola TaskForce! In this firmware version you will enjoy:
NVMe support: imaging of NVMe drives using M.2 extension module
Imaging of all sectors with data: skip empty sectors and image data only, one partition at a time
Improved interface: clickable and editable elements are now easily recognizable
and other features and improvements.
NVMe support
We are pleased to announce NVMe support in TaskForce! NVMe is the latest and greatest technology in the world of storage devices. NVMe drives achieve unprecedented speeds, which has made them very popular devices for laptops, desktop and corporate computers alike. NVMe drives can now be imaged with the help of our M.2 SSD extension module.
![]()
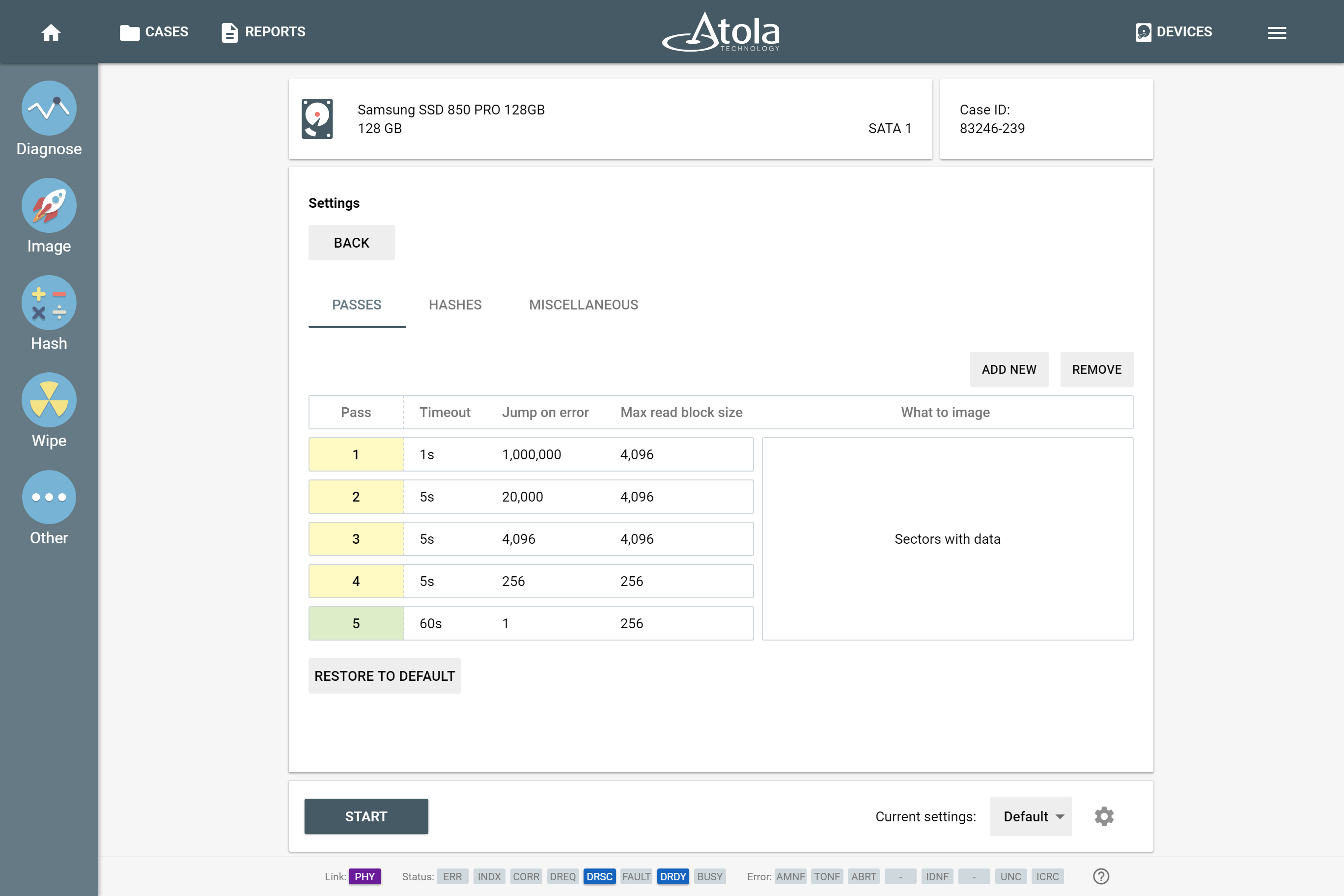
To image a drive:
- Plug M.2 extension module with NVMe drive to TaskForce while it is powered off
- Boot the system
- Click Image in the left-side menu
- Select the drive in Extension section of the Select source menu
- Click the target drive in the Select target menu
- Click Start to proceed with imaging
![]()
Imaging an NVMe drive
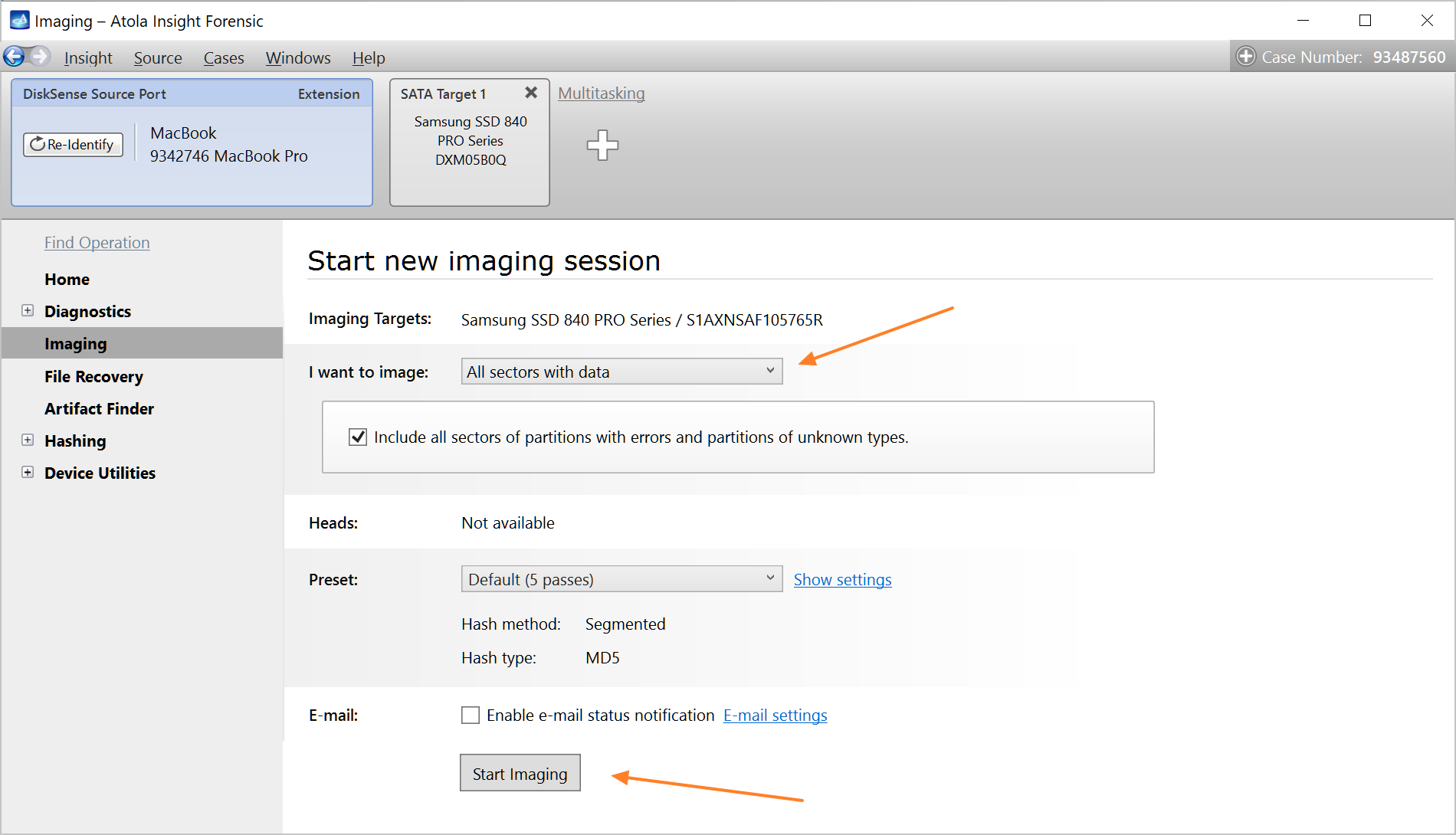
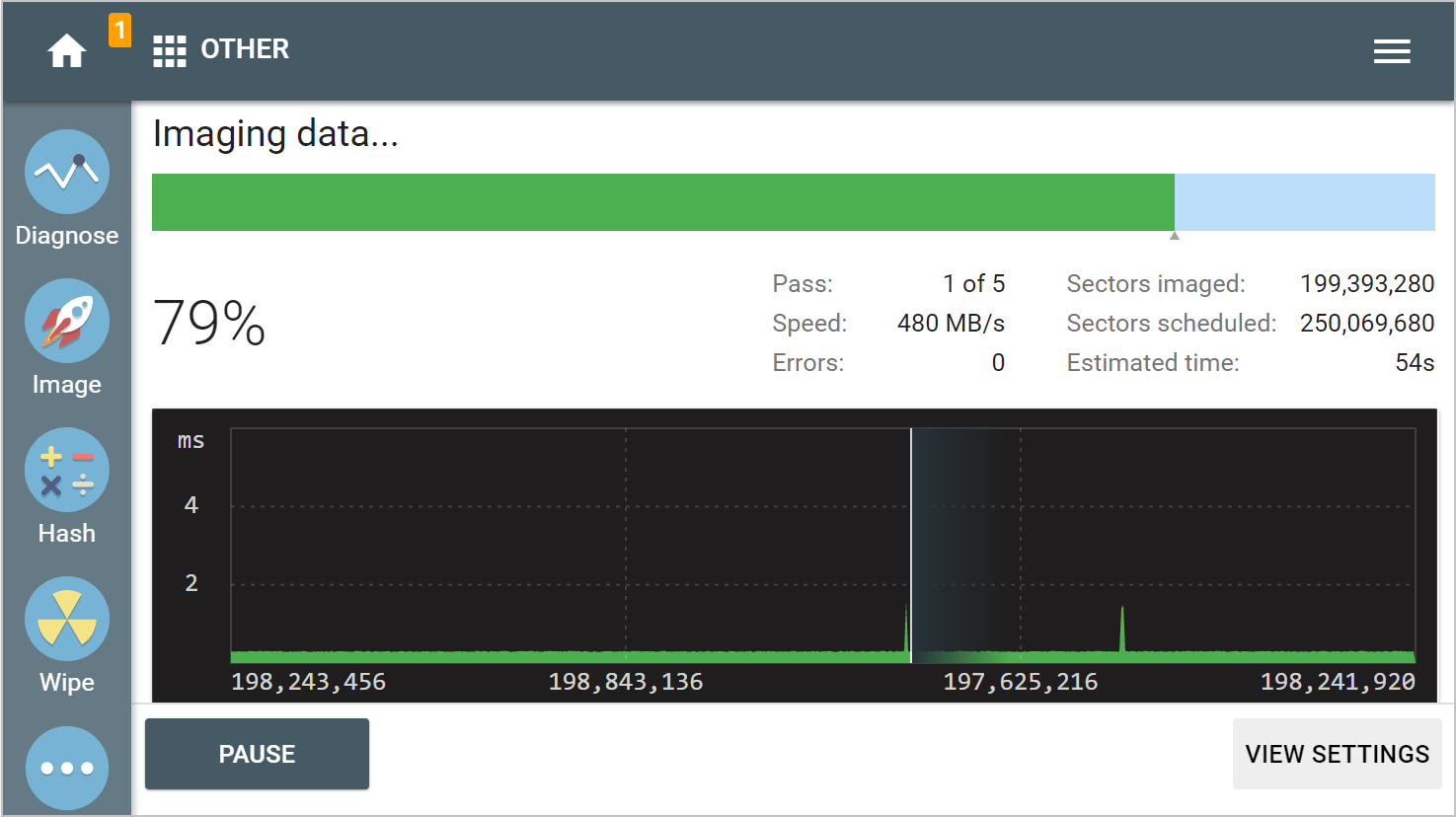
Imaging all sectors with data
We are extending selective imaging functionality and have made it possible to image only sectors containing data. This feature is supported in these file systems: NTFS, APFS, Ext 2/3/4, HFS, HFS+, ExFAT, FAT16, FAT32.
- Click Change button to adjust imaging settings
- In Passes tab, click on the value in What to image column
- Select Sectors with data
- Click Show button to preview the partitions on the source drive
- Click Start button to proceed with imaging
![]()
Imaging sectors with data (GIF)
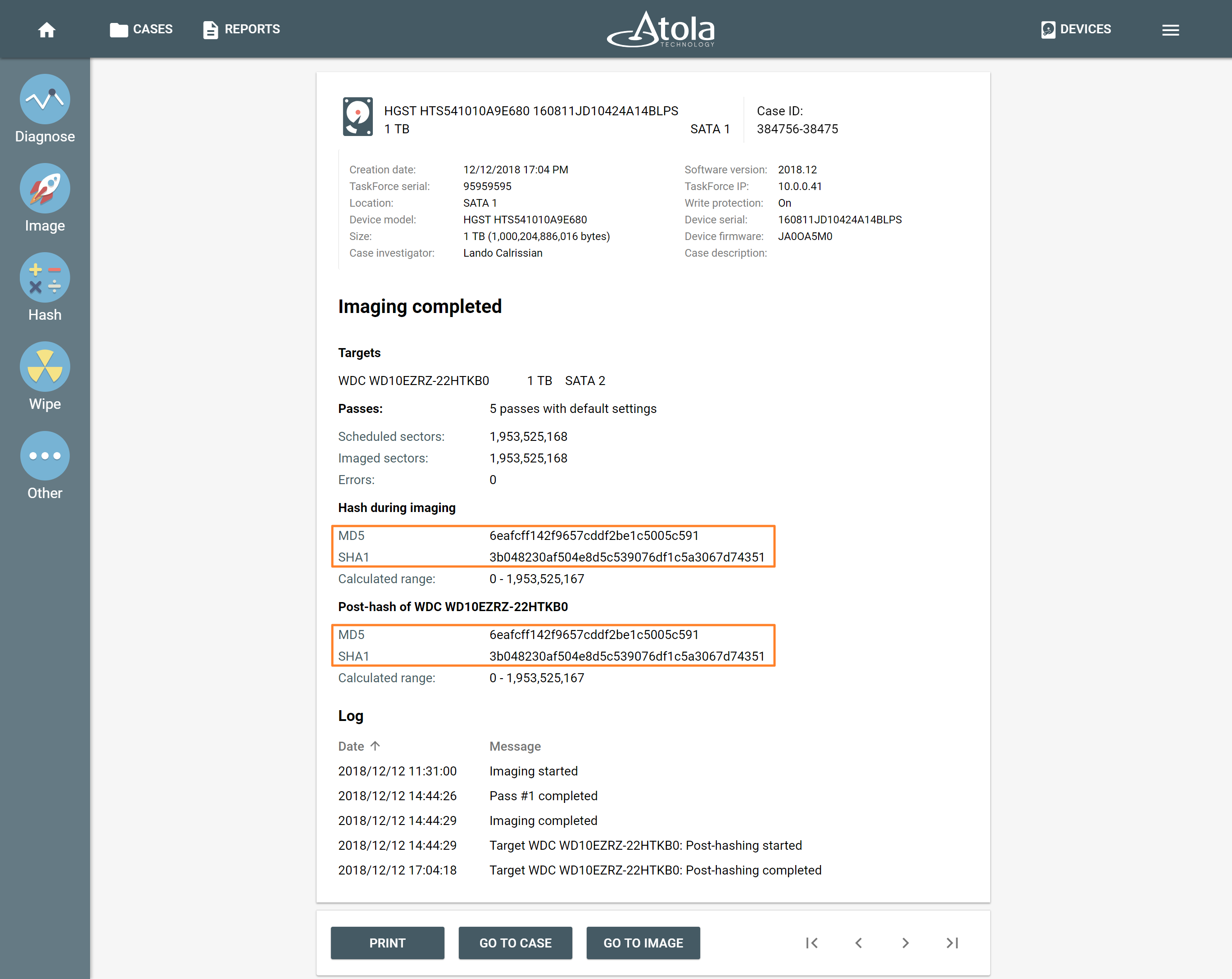
Improved user interface
In this release, we have improved the interface to help users easily identify clickable and editable elements. Pages are now centered for compact distribution of important elements and resemble a printed document layout.
![New user interface]()
New user interface
We have supported responsive design for smartphones so that the interface adjusts to screen resolutions and fits most of the important elements on the page.
![Smartphone UI]()
Smartphone UI
Other changes
Support of M.2, Thunderbolt, and Apple PCIe extension modules
Imaging
- Unclip HPA until power cycle on source drives
- Pause and Resume features support for pre-hash and post-hash calculation during an imaging session
- SAS port. Performance increase by 25%
- Improved imaging of damaged drives
- New setting Save report in the target folder when imaging to a file
- E01 metadata automatically filled with case ID, investigator, description from the case management system
User interface
- Short values supported (1K, 1M, 1G, 1T) in all LBA text boxes.
Example: 3M transforms into 3,000,000
4K sector size support on SATA, SAS, USB drives.
Wiping. Added methods: NIST 800-88, DOD 5220, Random, LBA Number.
System menu. Added Release notes page and Toggle full screen feature
Bugfixes
- USB devices. On certain devices, bad sectors were detected but not reported in the logs
- Warning when opening E01 file in Encase created by Atola TaskForce
- HPA/DCO indication missing on SATA devices plugged to SAS ports
- Issues identifying drives in PUIS mode
- Unclip HPA/DCO not working on IDE drives
- Several translation inaccuracies in the Chinese version
For the full list of new TaskForce features and fixes in this and previous releases, please read the changelog.
Where to buy
If you still do not have an Atola TaskForce and would like to place an order, this can be done directly via Atola Technology, or from a distributor near you:
http://atola.com/wheretobuy/
Please contact Atola Technology sales department to receive more specific information:
- Call us: +1 888 540-2010, +1 416 833-3501 10am – 6pm ET
- Or email us
P.S. Dear customers, we appreciate your feedback and take it into consideration when updating our products. Please feel free to write your thoughts and ideas in the comments section below.
The post Atola TaskForce 2018.12 release is out! appeared first on Atola Blog.